The Ascon family is specified in the following documents:
- Journal of Cryptology article: Ascon v1.2 (authenticated encryption and hash)
- NIST submission: Ascon v1.2 (authenticated encryption and hash)
- CAESAR submission: Ascon v1.2 (authenticated encryption)
Ascon's Permutation
All Ascon family members use the same lightweight permutation. This permutation iteratively applies an SPN-based round transformation a = 12 times (for pa ) or b ∈ {6, 8} times (for pb ). The round transformation consists of the following three steps which operate on a 320-bit state divided into 5 words x0, x1, x2, x3, x4 of 64 bits each:
- Addition of Round Constants: xors a round specific 1-byte constant to word x2.
- Nonlinear Substitution Layer: applies a 5-bit S-box 64 times in parallel in a bit-sliced fashion (vertically, across words).
- Linear Diffusion Layer: xors different rotated copies of each word (horizontally, within each word).

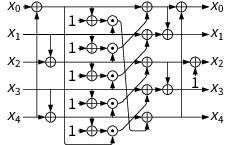
Ascon's permutation: ⊕ denotes xor, ⊙ denotes and, ⋙ is rotation to the right.
Ascon's Authenticated Encryption Modes
Ascon uses a duplex-sponge-based mode of operation for authenticated encryption. The recommended key, tag and nonce length is 128 bits. The sponge operates on a state of 320 bits, with message blocks of 64 or 128 bits. The encryption process is split into four phases:
- Initialization: initializes the state with the key K and nonce N.
- Associated Data Processing: updates the state with associated data blocks Ai .
- Plaintext Processing: injects plaintext blocks Pi into the state and extracts ciphertext blocks Ci .
- Finalization: injects the key K again and extracts the tag T for authentication.
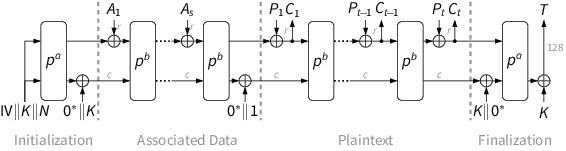
After each injected block (except the last plaintext block), the core permutation pb is applied to the complete state. During initialization and finalization, a stronger permutation pa with more rounds is used. The numbers of rounds a and b, as well as the sponge's rate and capacity, depend on the Ascon variant. The recommended parameters are:
| Cipher | Bit size of | Rounds | |||||||
|---|---|---|---|---|---|---|---|---|---|
| key | nonce | tag | rate | capacity | pa | pb | |||
| Ascon-128 | 128 | 128 | 128 | 64 | 256 | 12 | 6 | ||
| Ascon-128a | 128 | 128 | 128 | 128 | 192 | 12 | 8 | ||
Ascon's Hashing Modes
The Ascon family includes the hash functions Ascon-Hash and Ascon-Hasha as well as the extendable output functions Ascon-Xof and Ascon-Xofa with sponge-based modes of operation. Both provide 128-bit security with a hash size of at least 256 bits. The hashing modes use the same lightweight 320-bit permutation as the authenticated encryption modes.
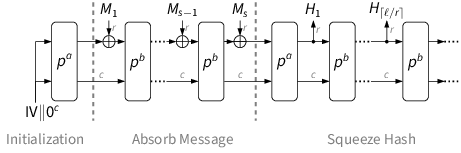
The hashing modes absorb the message M in 64-bit blocks Mi and finally squeeze the hash value H in 64-bit blocks Hi . After each absorbed or squeezed block except the last, the b-round permutation pb is applied to the state. The full a-round permutation pa is applied in the initialization and finalization, after the last message block:
| Algorithm | Bit size of | Rounds | |||||
|---|---|---|---|---|---|---|---|
| hash output | rate | capacity | pa | pb | |||
| Ascon-Hash | 256 | 64 | 256 | 12 | 12 | ||
| Ascon-Xof | arbitrary | 64 | 256 | 12 | 12 | ||
| Ascon-Hasha | 256 | 64 | 256 | 12 | 8 | ||
| Ascon-Xofa | arbitrary | 64 | 256 | 12 | 8 | ||
For details such as the IV and round constant values, padding rules or the (almost identical) decryption mode, please refer to the latest Ascon submission document.